This post is also available in: Bahasa Malaysia (Malay) Bahasa Indonesia (Indonesian)
When most people think of a “network hack,” they imagine a shadowy figure breaking into their office Wi-Fi from the parking lot. But here’s the reality: hackers don’t always need your Wi-Fi password to get into your systems. In fact, some of the most damaging breaches happen without the attacker ever connecting to your wireless network.
Let’s look at how they can do it — and how you can protect your business.
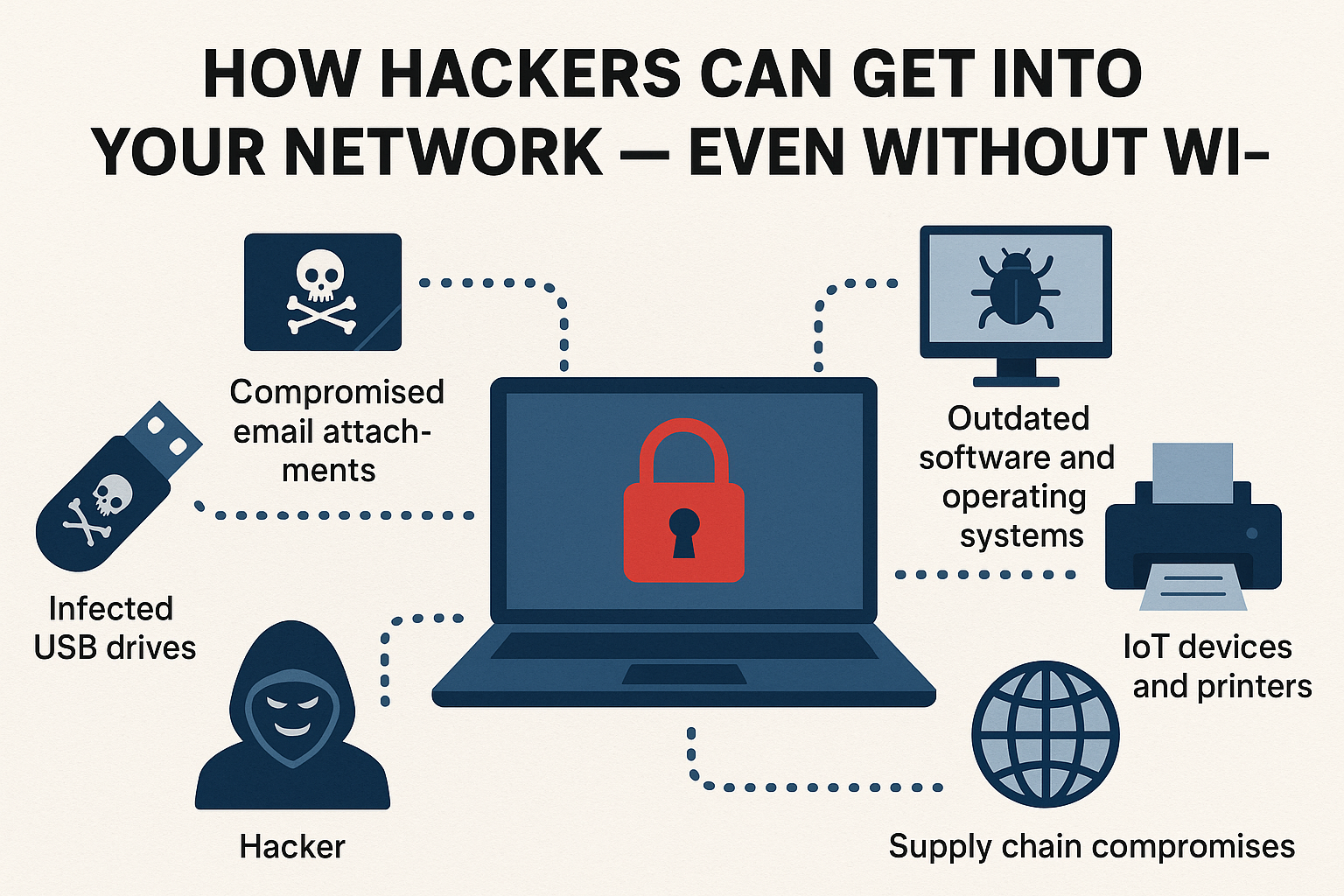
1. Infected USB Drives and External Devices
A classic but still highly effective method is the “USB drop”. A hacker leaves an infected thumb drive where someone in your office might pick it up — perhaps in the lobby, parking lot, or even mailed to your business. Once it’s plugged into a company computer, the malicious software installs itself and opens a backdoor into your systems.
Prevention tip: Disable auto-run features, block unknown USB devices, and train staff never to plug in unverified drives.
2. Compromised Email Attachments and Links
Phishing emails remain the number one entry point for cybercriminals. These messages often look legitimate, sometimes even appearing to come from trusted suppliers or government bodies. Clicking a malicious link or opening an infected attachment can install malware or give the hacker control over your machine.
Prevention tip: Use email filtering tools, keep antivirus up to date, and train your team to spot suspicious messages.
3. Outdated Software and Operating Systems
Hackers actively scan the internet for devices running outdated software. They exploit known vulnerabilities to gain access — no Wi-Fi required. A single unpatched accounting system, web server, or cloud application could give them an open door.
Prevention tip: Apply updates promptly, especially for critical security patches, and avoid running software past its support date.
4. Remote Desktop Protocol (RDP) Attacks
Many businesses enable remote desktop access for convenience. If poorly configured, hackers can brute-force weak passwords and log in directly from anywhere in the world.
Prevention tip: Use strong, unique passwords, enable multi-factor authentication (MFA), and restrict RDP access to specific IP addresses.
5. IoT Devices and Printers
Office printers, security cameras, and even smart TVs are often connected to the network but left unsecured. If these devices have default passwords or outdated firmware, hackers can use them as an entry point into your internal systems.
Prevention tip: Change default credentials, update firmware regularly, and place IoT devices on a separate network segment.
6. Supply Chain Compromises
Sometimes the hacker never targets you directly. Instead, they compromise a software vendor, IT provider, or cloud service you rely on, then use that connection to infiltrate your systems.
Prevention tip: Vet your suppliers’ security measures and monitor for unusual activity in vendor-managed systems.
The Bottom Line
Wi-Fi is just one door into your network — and often, it’s not even the easiest one for hackers to open. Small businesses must think about all possible entry points, especially those that don’t involve wireless access.
In our next article, we’ll break down “How a Simple Email Could Let Hackers Into Your System” and what you can do to stop it.
Did you find this article helpful? Please rate and also share your thoughts in the comments section below.
